Table of contents
OAuth stands for "Open Authorization,"
OAuth is an Open Standard and widely adopted protocol.
Used to Delegated Authorization: Lets third-party apps access user resources of a user, such as their data or services, without exposing the user's credentials.
Single Sign-On (SSO): Framework for secure authorization between multiple applications.
Protects User Credentials: Users don't share credentials; only access is granted.
Enables Data Sharing: Allows sharing of user data without exposing sensitive information.
Cross-System Authorization: Facilitates authorization across different systems.
Enhances Security: Improves security by limiting access and protecting user privacy.
Use Cases:
Data Access: Allows apps to access user data without having login credentials.
Single Sign-On (SSO): Enables users to log in once and access multiple services.
Security Benefits:
User Credentials: Kept secure, not shared with third-party apps.
User Control: Users decide what resources a client can access.
Common Applications:
OAuth is commonly used by applications that need to access user data from other services, such as social media platforms (e.g., Facebook, Google) or cloud services (e.g., Google Drive). It helps improve security by avoiding the need for the client to store sensitive user credentials and allows users to control which resources the client can access.
Social Media Platforms: Enables apps to access user data without passwords.
Cloud Services: Allows secure access to resources stored in the cloud.

Evolution from OAuth 1.0 to OAuth 2.0
Revolutionized authentication from previous method of username and password authentication because of its secuirty and flexibility.
OAuth 1.0's
complexity hindered widespread adoption.
Primarily used for web-based applications.
In 2012, OAuth 2.0
addressed these challenges, becoming a secure and flexible protocol used by major platforms like Facebook and Twitter.
focused on user authorization.
Used in various application types (web, mobile, desktop).
Fundamentals of OAuth 2.0
OAuth 2.0 facilitates secure data access without sharing passwords. It acts as a protocol for sharing user authorization across systems.
EXAMPLE
Scenario: "Login with Google"
User (Resource Owner): You, the person who wants to log in to a website or app.
Google (Authorization Server): Google serves as the trusted authorization server. It holds your user information and provides a secure way to verify your identity.
Website or App (Client): The application you want to log in to. It could be any website or service that offers "Login with Google."
Access Token (Authorization Token): Think of this as your virtual key. When you click "Login with Google," Google provides the website/app with a special access token.
Permission Request (Consent Screen): Before giving you the virtual key, Google may ask for your permission (like asking if it's okay for the website to access your email or profile).
Token Verification (Authentication): The website/app takes the access token and asks Google, "Is this token legit?" Google checks it, ensuring it's valid and issued for the right user.
User Logged In: If everything checks out, the website/app knows you're the real user, and you get logged in without entering a separate username or password.
Simplifying the Process:
Without OAuth2 (Traditional Login): You'd need a unique username and password for every website. It's like having a different key for each door.
With OAuth2 (Login with Google): You use your Google key to unlock the doors of various websites. No need to remember multiple keys (passwords).
This way, "Login with Google" not only saves you from creating and remembering numerous usernames and passwords but also keeps your credentials secure. You're essentially using your Google identity to access different online places.
Key components of OAuth include:
Resource Owner (User): The entity that can grant access to a protected resource. This is typically the end-user.
Client: The application requesting access to the user's resources. This could be a web or mobile application.
Authorization Server: The server that authenticates the user and obtains their consent to grant access to the client. It issues access tokens after successful authentication.
Resource Server: While not explicitly part of the authentication process, resource servers host protected resources. It validates the access token and serves the requested resource if the token is valid.
Access Token: A token representing the authorization granted to the client. It is sent by the client to access protected resources on behalf of the user.
The Role of Access Tokens
An access token in OAuth is a credential that represents the authorization granted to a third-party application.
enable applications to access a user's protected resources securely on user's behalf. Unlike passwords, they preserve user privacy by providing partial necessary information of the user's account.
When a user grants permission to a client application to access their resources (such as data or services) on a resource server, the authorization server issues an access token.
Key points about access tokens in OAuth:
Authorization Grant: The process begins with the client application obtaining an authorization grant from the resource owner (user). This grant is a permission given by the user to access their resources.
Token Request: The client sends this authorization grant, along with its own credentials, to the authorization server.
Token Issuance: If the authorization grant is valid, the authorization server issues an access token to the client.
Token Usage: The client includes the access token in the authorization header of its HTTP requests when accessing protected resources on the resource server.
Limited Scope: Access tokens often have a limited scope and expiration time to enhance security.
OAuth typically uses the Authorization header to carry the access token when making requests to protected resources. The format of the Authorization header in OAuth 2.0 is known as the "Bearer Token" and looks like this:
Authorization: Bearer <access_token>Bearer Token: The access token is often sent as a "Bearer Token," meaning it's included in the HTTP Authorization header preceded by the word "Bearer."
type of token: Bearer
acesss token
tokens expiration time
Access tokens play a crucial role in ensuring secure and authorized communication between different components of an OAuth-enabled system.
OAuth 2.0 and JSON Web Tokens (JWT)
Though distinct, OAuth 2.0 and JWT can synergize for secure third-party access.
JWTs can be used to represent access tokens,
WHY THEY ARE BETTER ALTERNATIVE
self-contained nature,
enhance security than opaque tokens
versatility in transmitting authorization information because they are compact and url safe
Ease of verification.
Authorization Server vs. Identity Provider
Authorization servers issue access tokens
Identity providers authenticate users.
These roles can merge in some cases(e.g. google), they are distinct in the OAuth 2.0 framework.
OAuth 2.0 Flows
OAuth 2.0 defines several authorization flows that enable a user to grant access to their resources without sharing their credentials directly. Here are some common OAuth 2.0 flows:
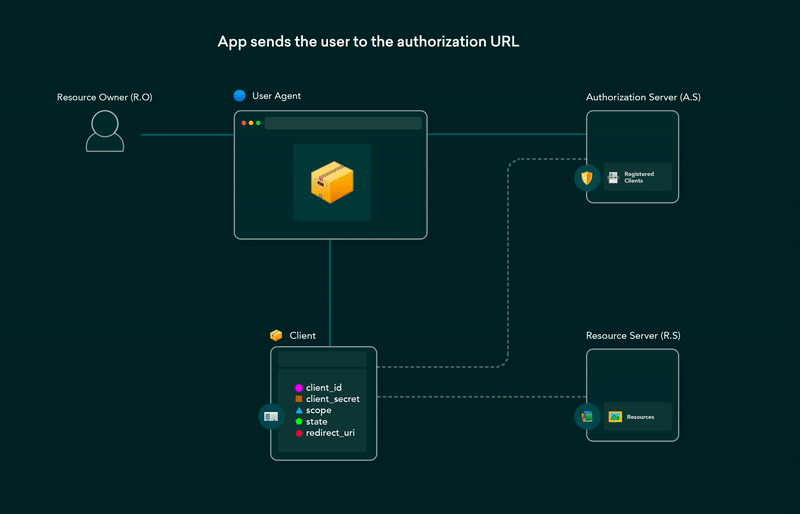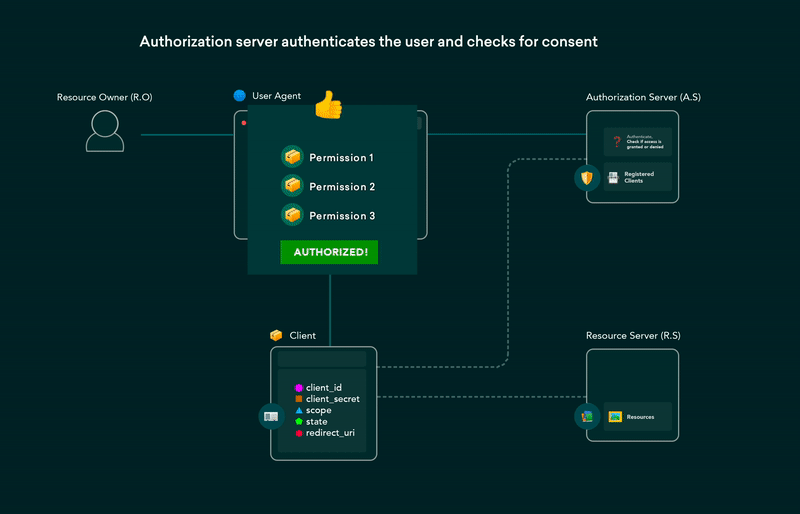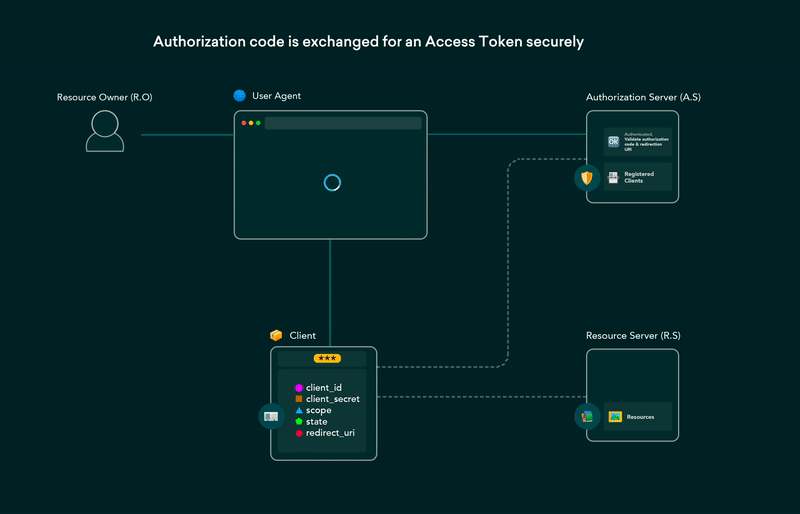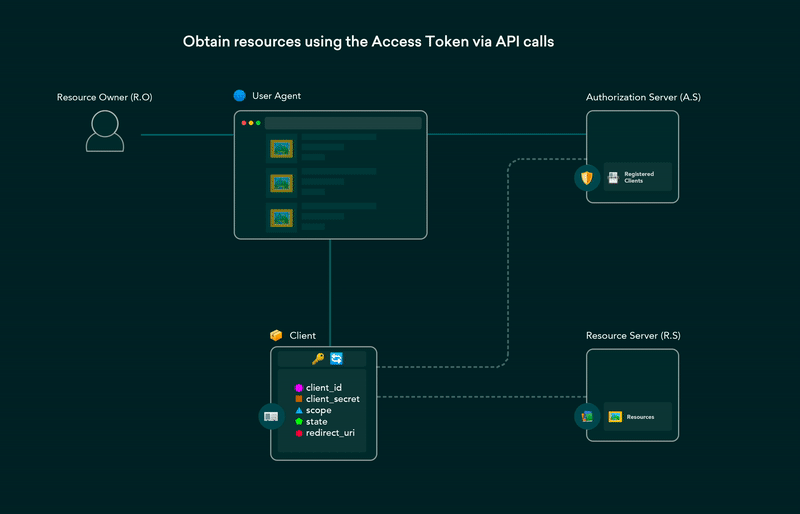
Authorization Code Flow:
The most secure and widely used flow.
Involves multiple steps: Authorization Request, User Authentication, Authorization Grant, and Access Token Request.
The client receives an authorization code, exchanges it for an access token, and often a refresh token.
use when application needs to access protected resources on behalf of the user
the user first authenticates with the IDP
and then the IDP redirects the user back to the application with an authorization code
the application then sends authorization code to the authorization server which validates the code and returns an access token and a refresh token to the application
the application can then use the access token to make requests to the resource server client
Implicit Flow:
Simplified flow suitable for public clients (like single-page apps) where the client cannot keep a secret.
The access token is issued directly without an authorization code.
It's suitable for scenarios where the client can't securely store a client secret.
Simplified version of Authorization Code Flow.
Authorization server redirects the user back to the application with an access token in the URL.
Less secure than Authorization Code Flow and not recommended for most applications.

Client Credentials Flow:
Used by confidential clients to obtain an access token.
The client authenticates directly with the authorization server using its client credentials (client ID and client secret).
Typically used for server-to-server communication.
used when the application does not access protected resources on behalf of the user instead the application needs to access its own protected resources
Application authenticates with the authorization server using client ID and secret.
Authorization server returns an access token to the application.

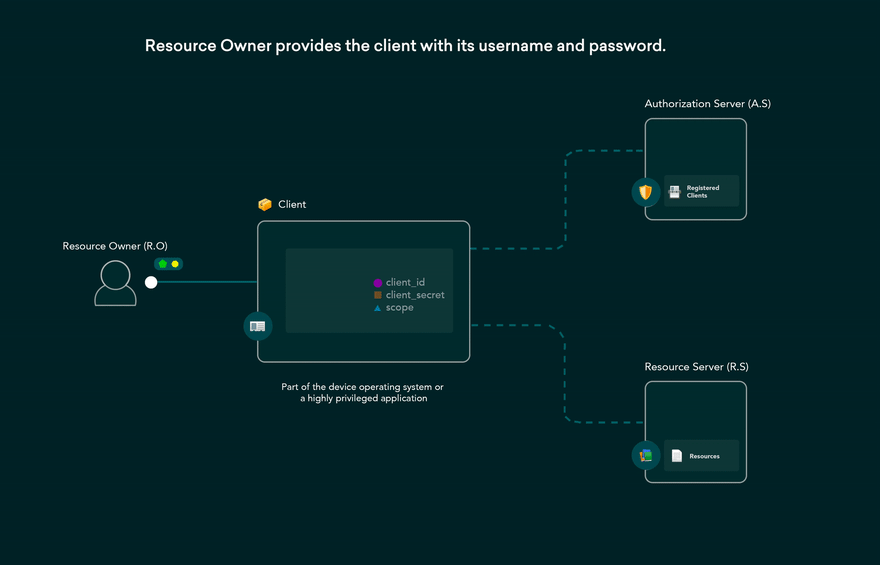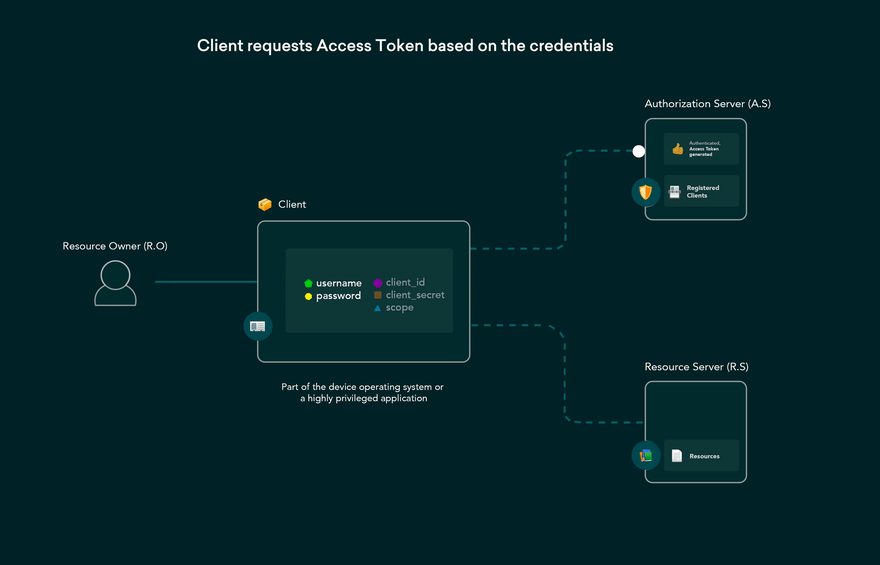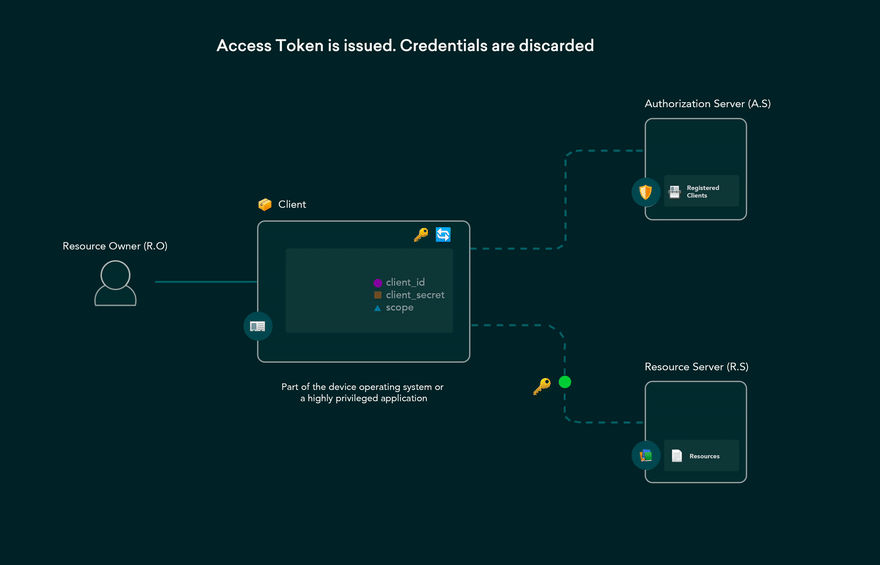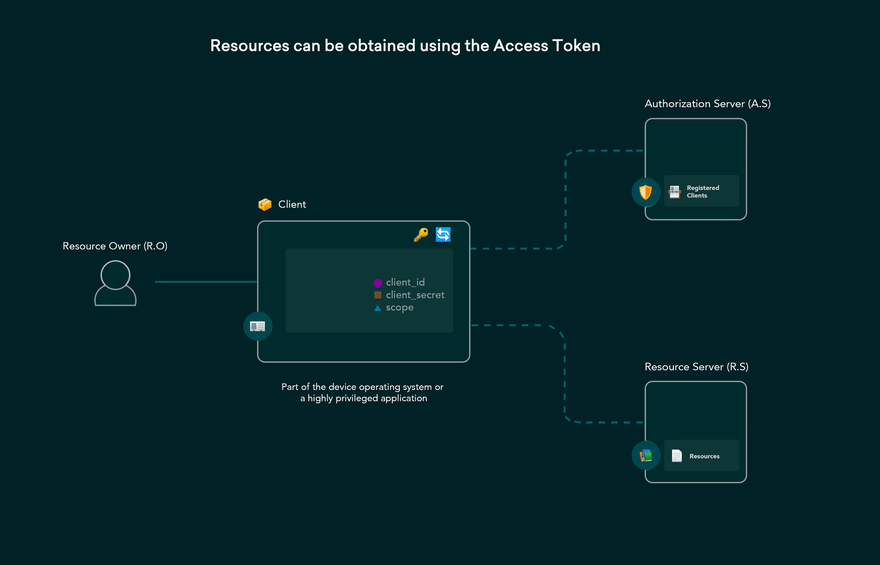
Resource Owner Password Credentials (ROPC) Flow:
The user's credentials (username and password) are exchanged directly for an access token.
Considered less secure and should only be used by highly trusted clients.
Not suitable for public clients or when the user's credentials should not be exposed.
Used when the application needs to access the user's protected resources.
User enters username and password directly into the application.
Application sends credentials to the authorization server.
Authorization server validates credentials and returns an access token and refresh token.
Device Authorization Flow (Device Grant):
Designed for input-constrained devices.
The user logs in on a separate device with better input capabilities, and a code is provided.
The code is then used by the device to obtain tokens.
Refresh Token Flow:
Used to obtain a new access token using a refresh token.
Refresh tokens are often issued along with access tokens during other flows.
Helps in maintaining continuous access without requiring the user to reauthenticate.
JWT Bearer Token Flow:
Used by clients to request an access token using a JSON Web Token (JWT) assertion.
The client includes a signed JWT assertion in the request for token exchange.
Authorization Grant Flow for Native Apps:
Similar to the Authorization Code Flow but designed for native apps.
Involves using a platform-specific mechanism to securely store credentials.
Each flow is designed for specific use cases and has its own security considerations. The choice of flow depends on the nature of the client application, the security requirements, and the capabilities of the devices involved in the authentication process.
OAuth VS Auth0
OAuth:
Definition: An open standard for access delegation commonly used for secure authorization.
Purpose: Enables third-party applications to access user resources without exposing credentials.
Usage: Often used for Single Sign-On (SSO) and secure data sharing between applications.
Auth0:
Definition: A third-party, cloud-based identity platform.
Purpose: Provides authentication and authorization as a service.
Usage: Developers can integrate Auth0 into their applications to handle user authentication, including social media logins, multi-factor authentication, and more.
In essence, OAuth is a protocol for authorization, while Auth0 is a service that implements OAuth and provides additional identity management features.
REFERENCES
